Begin
By default, a task will only run when a user is logged in. If you want to run a task after hours or over night, you will need to select “run whether the user is logged in or not” and “run with highest privilege’s”, so it runs in admin mode. Finally, you will need to add the user to the local admin group.
Some blog posts will say, you still can get a task to run if a regular user is not logged in. You can add the user to the local security group policy under “logon as a batch job” by going to secpol.msc, security settings, user rights assignment, logon as batch job, and add the user. I tested this multiple times and could not get this method to work when attempting to run a PowerShell script. Perhaps, this only works for true batch scripts.
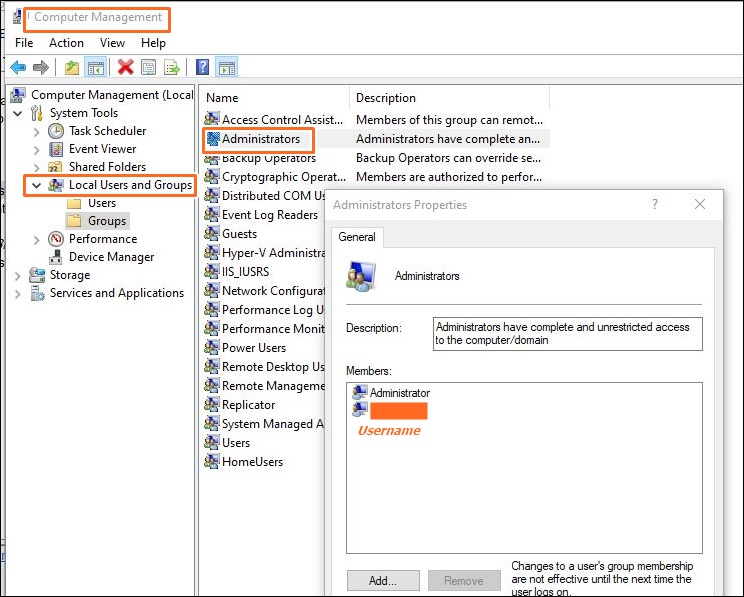
Let’s assume, I want to run a PowerShell script every hour of every day (i.e. 24 x7). First, check if your user is a local administrator. Go to Computer management, system tools, local users and groups, administrators. Verify he is included.
Run the task scheduler and select create a task.
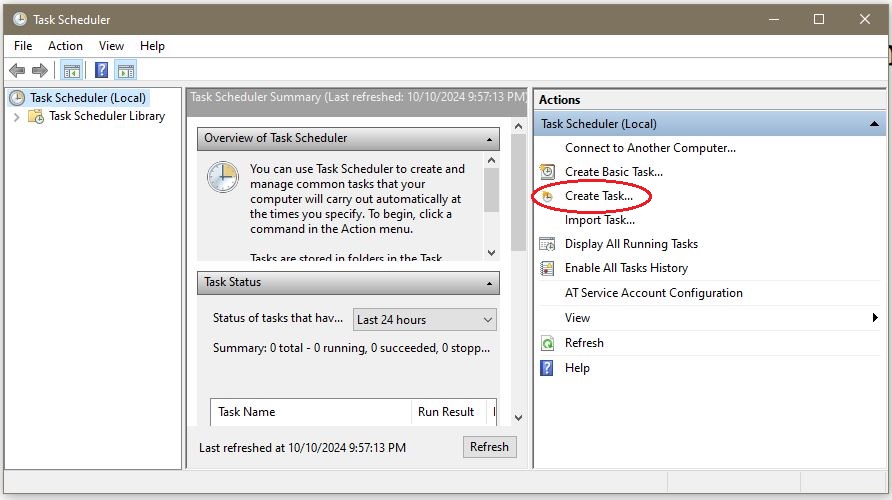
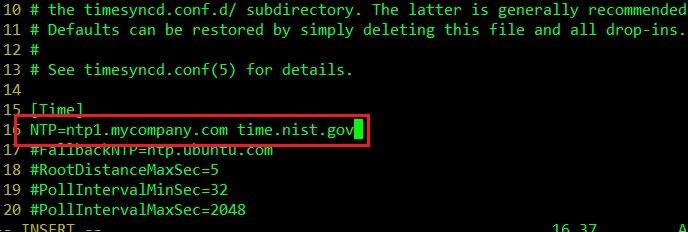
General Tab
Configure the Name, User account, Run whether the users is logged on or not, and Run with highest privileges, as it needs to run in admin mode when the user is logged out. Next, select Configure for Windows 10.
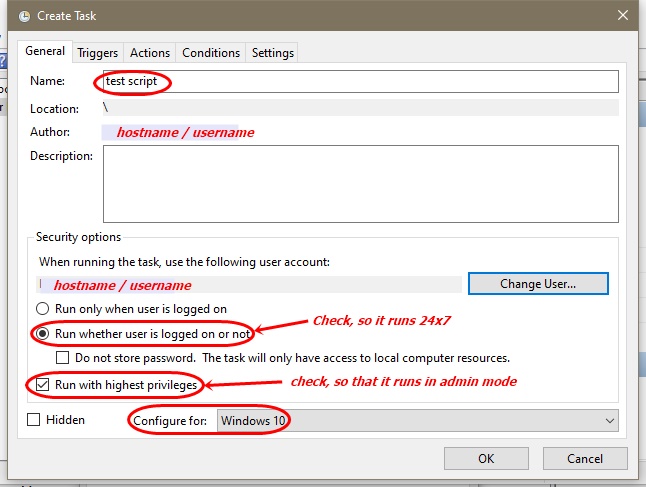
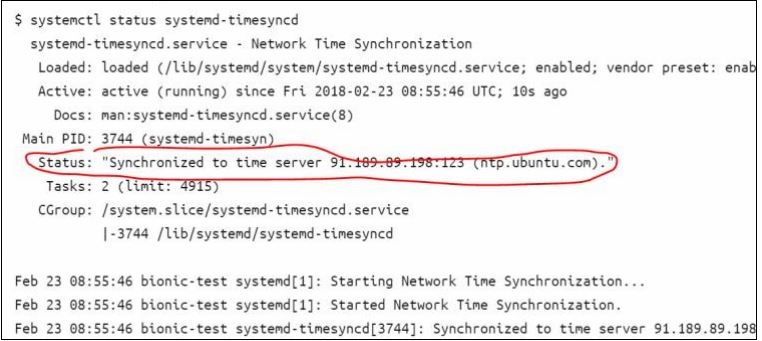
Triggers Tab
Select to run starting at 1:00 PM, every hour, and verify the task is enabled.
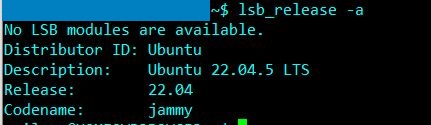
Action Tab
The script must be stored under the local user’s profile to get it to execute!! i.e. C:\users\username\tasks\yourscript.ps1.
Program: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Argument: -nologo -ExecutionPolicy Bypass -windowstyle Hidden -file C:\Users\user1\scripts\report.ps1
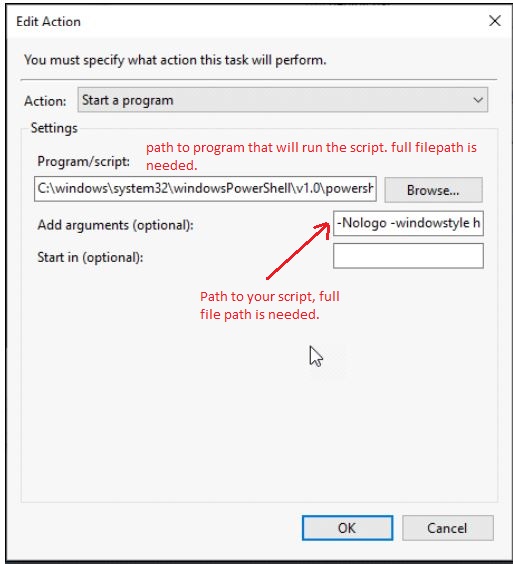
Common PowerShell arguments are:
- -NoProfile, meaning do not load the users profile (use when you have custom setting in the script).
- -ExecutionPolicy Bypass, means allow the script to run with no conditions (i.e. it is not signed).
- -Windowstyle Hidden, means do not display the PS window.
- -nologo, means to suppress the PS copyright info when PS starts (provides a cleaner process).
- -file /path/filename.ps1, enter full path to your script.
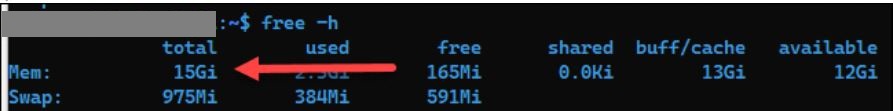
Conditions Tab
Make no changes.
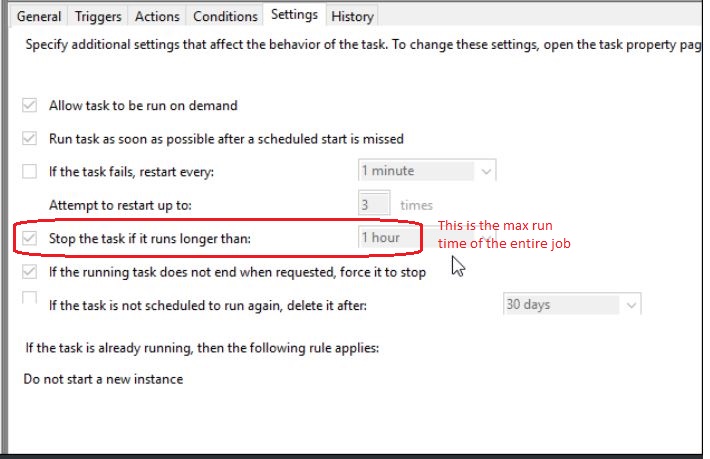
Settings Tab
Make no changes. Do not enable “if task fails. then restart”. If your password expires, it will keep locking your AD account.