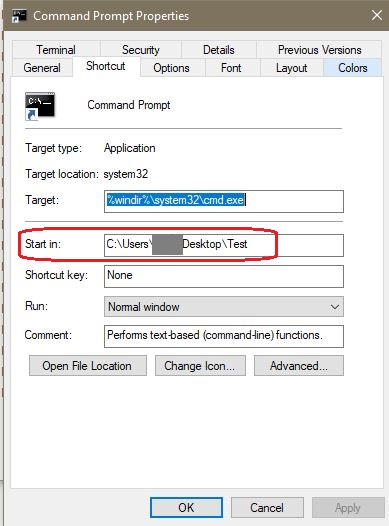
Change Default Startup Path for Command Prompt
Right click on the command prompt then select properties. On shortcut tab, change “Start in:”
Yet another food & tech blog
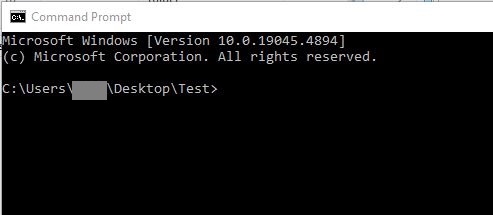
Right click on the command prompt then select properties. On shortcut tab, change “Start in:”



File encryption adds a level of security to your critical files. In Windows, you can create an encrypted folder and it will auto encrypt any files you drop into the folder.
Windows uses the Encrypted File System (EFS) platform. The first time you encrypt a file, it will auto generates a key set and a certificate. Windows manages the encryption for you on the backend. In other words, once you set it all up, it will automatically decrypt a file when you open it, and encrypt it when you close the file.
After you set up a folder in windows and encrypt it, any files you drop into that folder will automatically be encrypted too. No need to set the encryption on each file.
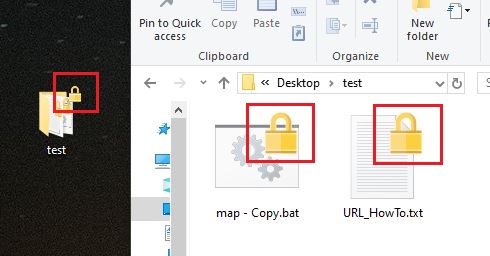
Does the folder or file has a lock on it?
An alternate method, is to go to the file, right click, select details, check the attributes for the E flag. (Note: The A flag means the archive bit is set).
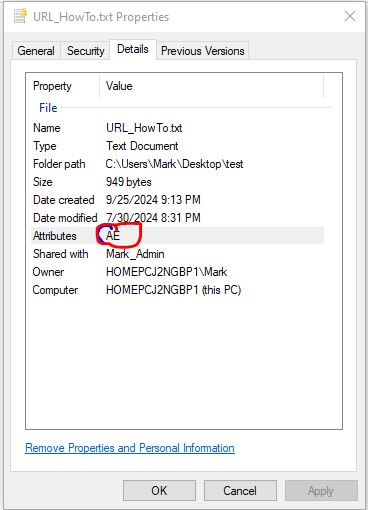
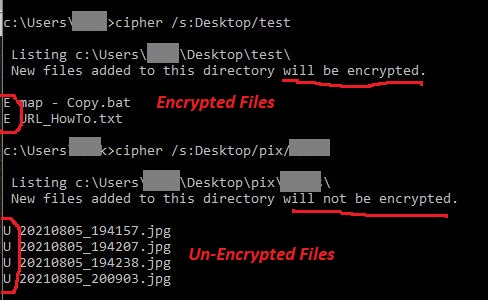
Finally, you can open a command prompt and run cipher.
ciper /s:Users/user1/Desktop/testHere are two folders, one has encrypted files inside it and one does not.
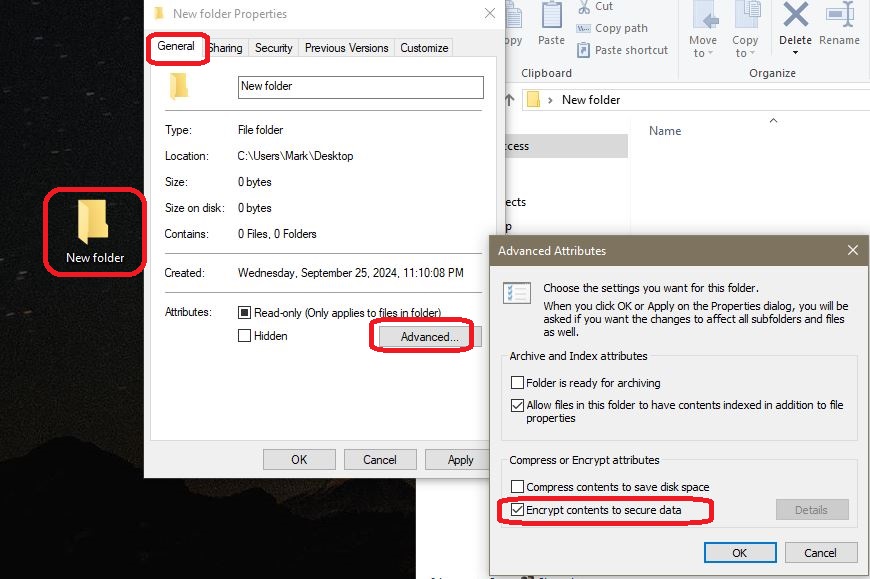
The easiest way to encrypt multiple files is to create an encrypted folder and drop files into it. Make a new folder on the desktop, right click on folder, select properties, go to general tab, select advanced button, and check the encrypt box.
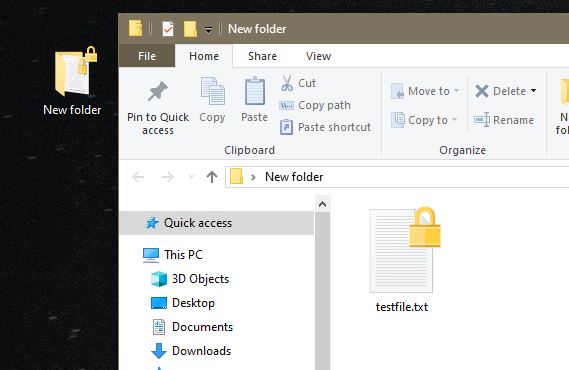
After you see the lock icon on the folder, this means the folder is encrypted. Any files you drop into it, will automatically be encrypted too and will display the lock icon. If you drag the the file outside the folder, it will remain encrypted.
Note: the lock symbol does not always show up right away after you encrypt a file/folder, don’t panic.

Crontab stand for CRON table and it is the primary task scheduler for Linux. The CRON daemon runs every minute and checks each user’s crontab (and the system crontab) for scheduled jobs. CRON will auto start on reboot and record to syslog natively when a job runs. CRON will send “standard out” and “errors” to the scheduled user’s mail account at /var/spool/mail/user. By default, CRON uses the bash shell to execute commands.
There are two types of crontabs; user crontabs and system crontabs. The system wide CRONTAB jobs are stored in /etc/crontab. It is used to execute scripts that apply to the system change or all users. It requires an additional field in the crontab called a user field. This article will be focused on setting up a user’s crontab.
If your script runs successfully from the command line, but not when it is run as a CRONTAB job, it is because crontabs are executed by the user CRON. That user has limited rights and does not have the same environmental variables as a regular user. It is recommended to always use absolute paths for shell, commands, and scripts, in your crontab.
MIN HRS DOM MON DOW <Conditional Statement> <Command> <Argument>
0 8 * * tue [ `date +\%d` -le 7 ] && /bin/bash /home/user/script.sh >/dev/null 2>&1crontab -lcrontab -eNOTE: Some documents say, after you save and install a new CRONTAB, you need to reload the CRON service by running “service cron reload”. But, other documents say you do not to perform this action.
crontab -rsudo crontab -u user -lNOTE: CRON uses military time, which is using hours 0 to 23.
HR MIN DOM MON DOW
* * * * * /bin/bash /home/user/script.sh (every minute of everyday)
0 0 * * * /bin/bash /home/user/script.sh (midnight everyday)
*/5 * * * * /bin/bash /home/user/script.sh (every 5 minutes)
0 17 * * * /bin/bash /home/user.script.sh (5pm everyday)
0 7,19 * * * /bin/bash /home/user/script.sh (7am & 7pm everyday)
0 7 2-4 * * /bin/bash /home/user/script.sh (7am, 2nd,3rd,4th of the month)
0 21 * * 1-5 /bin/bash /root/test.sh (9pm, Monday thru Friday)
0 7 * * tue [ $(date +\%d) -le 7 ] && /bin/bash /root/script.sh (7am,1st Tue of month)0 7 1 * Mon /bin/bash /home/user/script.shBe careful when writing cron jobs. For the day of week and day of month fields, crontab should be interpreted as AND statements. The command will run when either field matches the current time! This example would not run a script on the first Monday of the month. Rather, this job runs on the first day of the month and every Monday.
*/35 * * * * /bin/bash /home/user/script.shSkip values can only operate within the time period they´re attached to. The above will not execute every 35 minutes. Rather, it will execute at 0 minutes and 35 minutes each hour.
@reboot /usr/bin/perl -w /data/nfsen/bin/nfsen start “/usr/bin/perl -w” mean to enable and print warning messages.
30 6 * * * /usr/bin/python3 /root/script.py | mail -s "Results" user@company.com30 7 * * * /bin/bash /home/max/backup.sh 2>&1 | /usr/bin/logger -t ossecScreen output and errors are recorded in the user’s mailbox at /var/spool/mail/<user>. When scripts run overnight, output to the screen (stdout) is not needed. It is common to send standard out to /dev/null and errors to a custom log file. You will need to ensure that the log file does not grow out of control.
2>&1 means to send any errors to the same location as standard out. Order matters! you can not send errors to location that does not exist. Be sure to identify the location of the screen output first.
>/dev/null (delete std out)
>/dev/null 2>&1 (delete std out & errors)
>/dev/null 2>>/home/user/err.log (del std out, append err to log)
>/dev/null 2>>/var/log/syslog (del std out, append err to syslog)
>>/home/user/file.log 2>&1 (append std out & err to a custom log)https://krisjordan.com/blog/2013/11/04/timesaving-crontab-tips
Although PowerShell has made progress over the last few years as the preferred command line tool, I find that knowledge of the original command line is still very valuable. You can use the command line to quickly get system information or write batch scripts to automate simple tasks.
Most commands can be run as a regular user. But, as always, depending on what you are doing some commands may need to be run at an elevated prompt. To see all available commands, type “help”. To see help about a specific command use “<command> /?”.
| cd /d H: | Change drive to H: drive |
| cd \ | Change directory to C:\ |
| help | See all commands. |
| <command> /? | Get help about command <command>. |
| net user administrator /active:yes | Enable the hidden Administrator acct (run cmd as admin). |
| gpupdate /force | Update the user’s group policies. |
| net user username1 /domain | Get current user details (last logon, passwd age, etc). |
| gpresult /user <user1> /r | more | Get a list of the user’s domain groups. |
| psloggedon \pcname or ip | See who is logged in (sys internals). |
| net users | print a list of all system users. |
| sc query | more | Display status of active services. |
| net localgroup administrators | List all local administrators. |
| net localgroup “remote desktop users” | List users allowed to login remotely. |
| dir | Display files in the current folder. |
| cipher s:/<Folder name> | Check if a folder/file is encrypted. |
| cipher /c | Display info on the encrypted file. |
| mkdir | Make a Directory |
| find or findstr “Find” | Find all lines with the word “joe”. |
| del newfile.txt | Delete the file newfile.txt. |
| move [source] [ target] | Move file to new location. |
| fc /a monthly.txt sales.txt | Compare two text files. |
| robocopy /s [src] [dst] | Copy directories except empty ones. |
| msinfo32 | Launch the system info GUI. |
| hostname | Display the name of the computer. |
| wmic cpu get numberofcores, NumberOfLogicalProcessors | Display # of CPU cores and logical processors. |
| wmic /node:10.10.56.10 bios get name, version | Display BIOS name & ver. from a remote PC. |
| wmic os get caption, version | Display OS name and version. |
| wmic computersystem get manufacturer, model | Display PC manufacturer and model. |
| systeminfo <hostname> | find “OS Name” | Display the OS Name only. |
| net share | List all files on the system that you are sharing. |
| msconfig | Launch sys config GUI. Manage startup programs. |
| taskkill | Kill running processes. |
| shutdown /r | Shutdown and reboot the pc. |
| mstsc /admin | Start an RDP session. |
| tasklist | display running processes. |
| wmic process get description, executablepath | display running executables. |
| schtasks /query | more | Display scheduled tasks |
| ping -a | Test network connectivity and resolve DNS. |
| ipconfig /all | Displays current IPv4, DNS server name, and Gateway router IP, and other info. |
| nslookup | Returns an IP address or a name. |
| tracert <url> | Trace & displays path to reach an internet host. |
| netstat | Check the UDP/TCP connections. ( See Article) |
| route print | List routing table. |
| arp -a | Get address resolution table. |
| netsh | Change network setting, like whether to use DCHP (See below). |
| nbstat | Display stats and current connections using NetBIOS over TCP/IP. |
Run these commands at an elevated prompt.
Set a static IP
netsh interface ip set address name="Local Area Connection" static 192.168.0.1 255.255.255.0 192.168.0.254Set DHCP from a static IP address
netsh interface ip set address name="Local Area Connection" source=dhcpSet A Primary DNS Server To a static IP
netsh interface ip set dns name="Local Area Connection" static 192.168.0.250Set the secondary DNS server to a static IP
netsh interface ip add dns name="Local Area Connection" 8.8.8.8 index=2Set your DNS settings to be assigned dynamically
netsh interface ip set dnsservers name="Local Area Connection" source=dhcp
Ansible gives you a powerful option to run commands ad-hoc. This negates the need to write a script, if you only need some quick information. There are two separate options for gathering data via ad-hoc. If you are running just a single command than use the ‘command’ module. If you need to run multiple commands, use the ‘shell’ module.
You may or may not need to reference the your inventory file, if you are using DNS names. If you are using IP addresses, then you probably do not need it.
-m = module (shell or command)
-a = argument (command you want to run on the remote system).
ansible -i inventory.ini -m command -a 'ip a' server1,server2ansible -i inventory.ini -m shell -a 'hostname ; ipa | grep 10.10 ; df -h | grep /dev/mapper ; lsb_release -a' server1
Password manager databases, asynchronous keys, digital signatures, and MFA recovery passcodes are designed to identify you, decrypt files, or help you recover from a failed 2FA login. Care must be taken to protect these digital items so they do not fall into unwanted hands.
The below techniques are not a cure all, and other options should be considered. But, these are basic beginning steps that can be taken to help keep your data private.
What ever options you choose, always make sure to BACKUP your data on a flash drive and store it in a “real world” safe. If keys, digital signatures, databases are lost or corrupted, there is no method to recover them.
Place your password database or asynchronous keys in a hidden folder. In Linux, to make a hidden folder, use a dot in front of the directory name like”.ssh”. To make a folder hidden in Windows, right click the folder, select properties, to go the general tab and select “hidden”. Although this method does not provide much protection by itself, it is a good starting point.
Change permissions on the files or folder so that only your account can access it. Use an explicate deny to all users including the system and administrator accounts. In Linux, this means changing a file’s rwx permissions to something like 400. In Windows, files are inherited by the parent folder. Right click on file, select properties, select, security tab. Under the “Group or username” section, select the edit button. Highlight each account, except your account, and select “Remove”.
After initially setting up an account on an application or website, you may given recovery or one-time authentication passcodes. This is an backup procedure to grant you access to the application in the event of an emergency that your regular MFA fail to work. Rather than printing these codes to PDF and keeping them on your PC. Print the passcodes to paper and store them off the network in a physical “real world” safe.
In asymmetric cryptography, you have a public key and a private key. The private key is to remain confidential. To help protect your private key, you can add a passphrase to it. A passphrase is a password for your private key. When used in conjunction with other security features, it may help slow down attackers. They will have to crack, yet another password, before they can access the key.
Store important files in an encrypted folder. In Windows, any file dropped into an encrypted folder will automatically be encrypted too. Simply right click on a folder, select properties, go to general tab, select advanced attributes, and select “Encrypt contents to secure data”. The Microsoft OS will automatically take care of encrypting and decrypting the folder and contents when it is accessed locally.
Ensure that your password manager database is encrypted. If you are using KeePass it is automatically encrypted when the database is generated.
Store the private key or database on a portable flash drive or YubiKey and only plug it in to your computer when you need to access it. For added safety, encrypt the flash drive.